You haven't signed in yet, you can have a better experience after signing in
 Sticky Password Professional Password Manager Software
Sticky Password Professional Password Manager Software

Activity Rules
1、Activity time:{{ info.groupon.start_at }} ~ {{ info.groupon.end_at }}。
1、Activity time:cease when sold out。
2、Validity period of the Group Buying:{{ info.groupon.expire_days * 24 }} hours。
3、Number of Group Buying:{{ info.groupon.need_count }}x。
Please Pay Attention
1、Teamwork process: Join/initiate a Group Buying and make a successful payment - Within the validity period, the number of team members meets the activity requirements - Group Buying succeeded!
2、If the number of participants cannot be met within the valid period, the group will fail, and the paid amount will be refunded in the original way.
3、The number of people required and the time of the event may vary among different products. Please pay attention to the rules of the event.
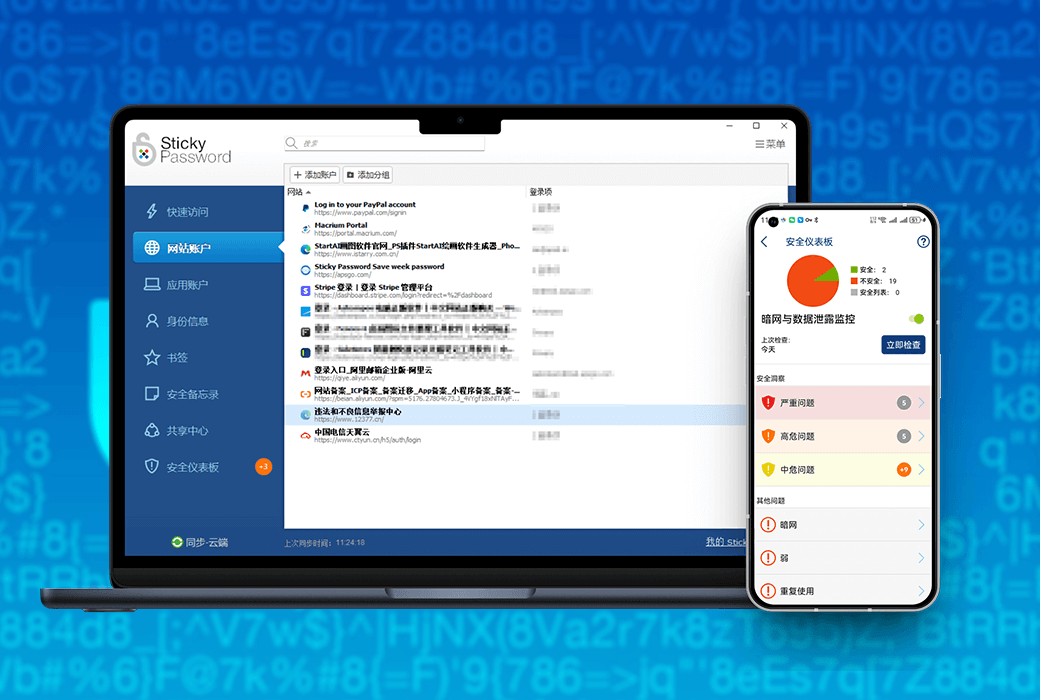
Sticky Password: Your digital life password guardian
In the digital age, managing numerous complex passwords has become a challenge. Sticky Password is an advanced password manager that provides you with a comprehensive solution to make your digital life more secure and convenient.
Main features:
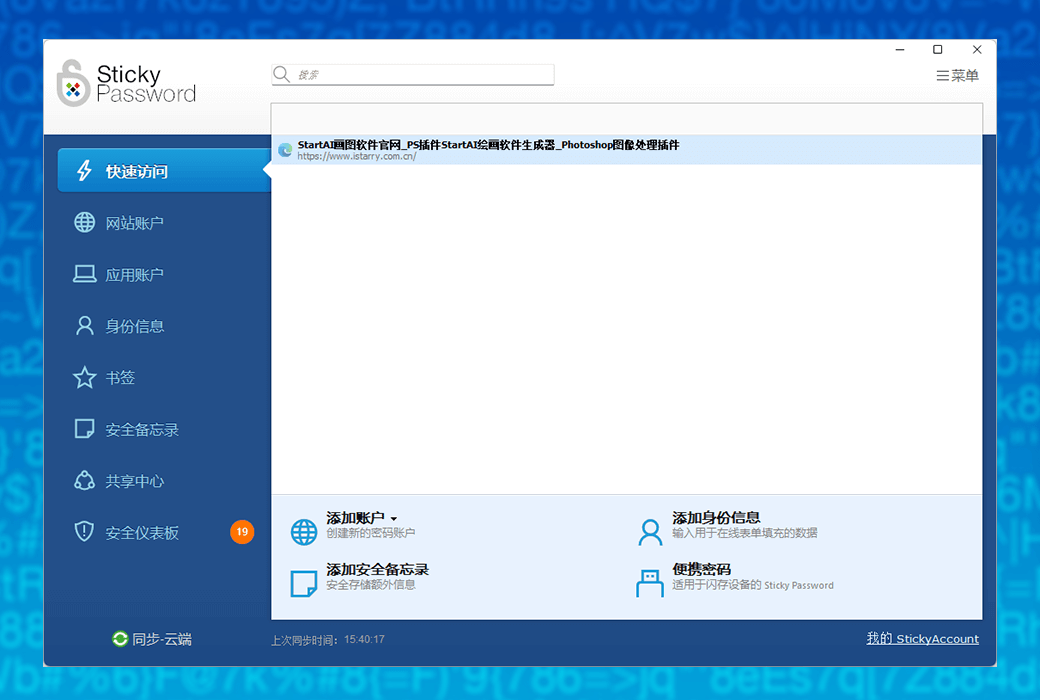
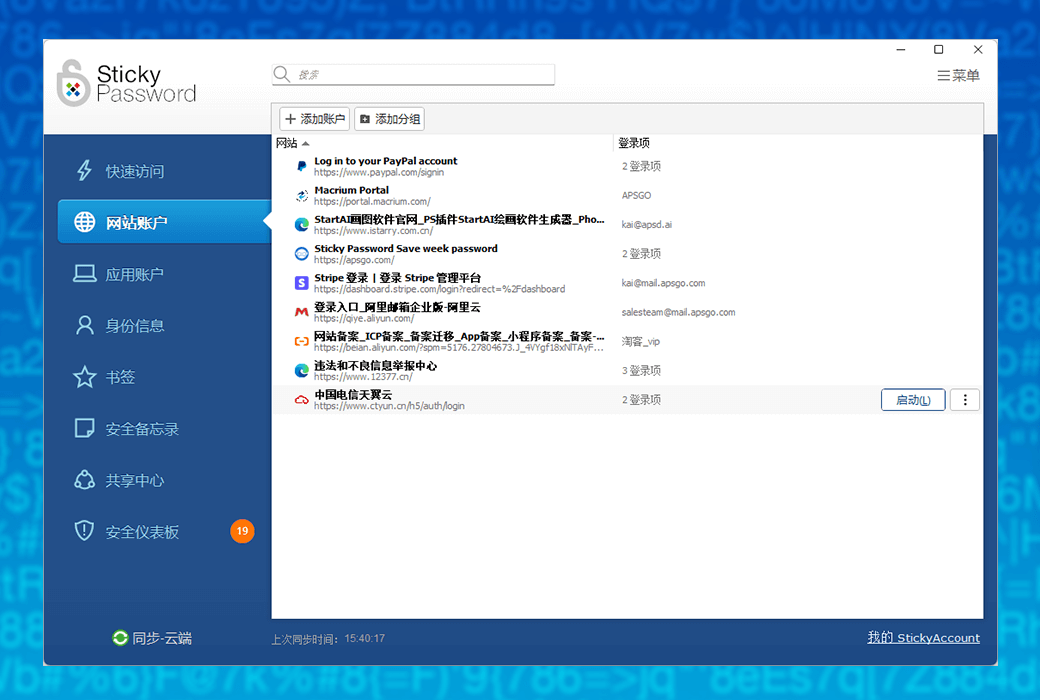
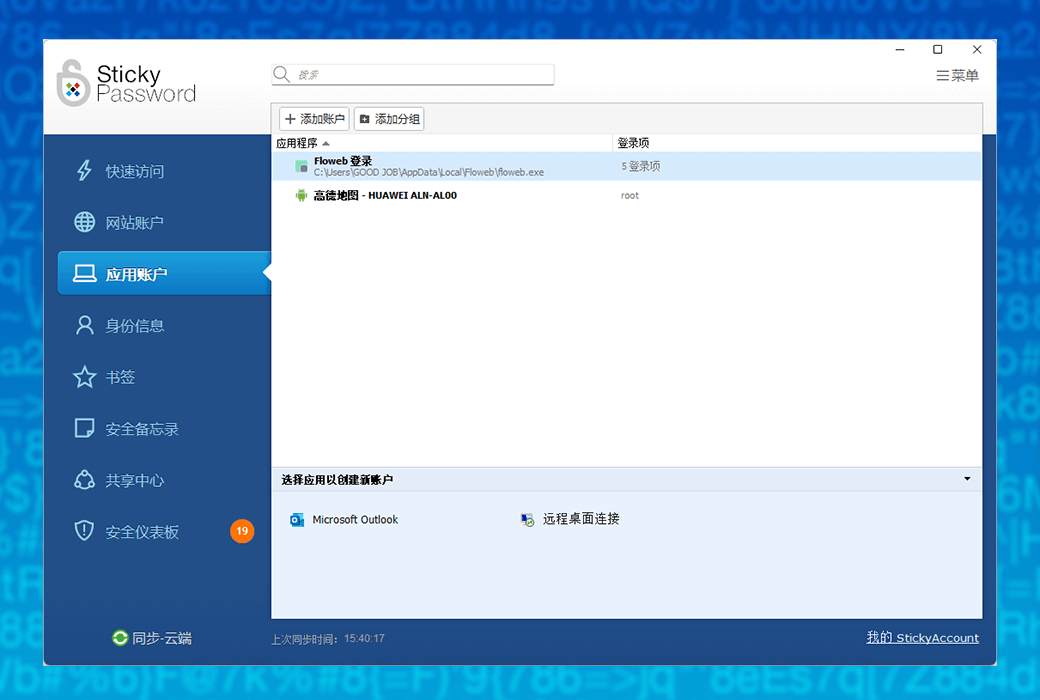
- Full platform supportSeamless synchronization of Windows, Mac, Android, and iOS devices, allowing you to easily access your password no matter where you are.
- One click automatic fillingAutomatically and accurately fill out online forms, saving you time and improving efficiency.
- Strong Password GeneratorIntelligent creation of complex and difficult to crack passwords to ensure account security.
- Crypto VaultSafely store your credit card information and important data, support one click payment, convenient and fast.
- Dark Web Monitoring AlertReal time monitoring of whether your password appears on the dark web, notifying you of potential security risks as soon as possible.
- Flexible synchronization optionsProvide multiple synchronization methods such as cloud synchronization, local Wi Fi, and manual offline to meet the needs of different users.
- Access permission managementGranting trusted individuals access to your account in emergency situations and flexible permission settings.
- Multi browser compatibilitySupport mainstream browsers such as Chrome, Firefox, Safari, etc., cross platform protection for your internet security.
- Biometric recognition supportQuickly unlock through fingerprint or facial recognition, adding an additional layer of security.
- social responsibilityBy purchasing the premium version, you not only receive more comprehensive services, but also contribute to the protection of endangered manatees.
User reviews:
Based on over 8200 real user reviews, Sticky Password has won high recognition from users for its ease of use, efficiency, and security. It is not only a password management tool, but also a powerful assistant for your digital life.
Sticky Password makes password management simple and makes network security within reach.

Official website:https://www.stickypassword.com/
Download Center:https://stickypassword.apsgo.cn
Delivery time:24-hour automatic shipping
Operating Platform:Windows、macOS、Android、iOS
Interface language:Supports Simplified Chinese interface display and other language options.
Update Description:Lifetime version manufacturers promise to purchase the software once for lifetime use and updates.
Trial before purchase:Free trial is available before purchase.
How to receive goods:After purchase, the activation information will be sent to the email address at the time of placing the order, and the corresponding product activation code can be viewed in the personal center, My Orders.
Number of devices:You can use Sticky Password on all your devices and synchronize data between different devices.
Replace computer:Uninstall the software on the original device and log in to the account on the new device.
Activation guidance:https://stickypassword.apsgo.com/#faq1736
Special note:Please make sure to remember that if you forget the 'master password', it cannot be retrieved. The lifetime license includes 1 year of ARC dark web monitoring service.
reference material:https://www.stickypassword.com/help/dark-web-monitoring-1140,https://www.stickypassword.com/help/what-is-a-stickyaccount-1008?action=faq1008&lng=en

Any question
{{ app.qa.openQa.Q.title }}
What can you do when Sticky Password detects a threat?
Now two layers of defense are provided. Notify users immediately when the leak monitoring report involves a leak incident of your service, while the dark web continues to scan the tents in the published data dump on hacker forums and dark web monitoring markets. They collectively provide broader visibility, covering the entire lifecycle from initial discovery to underground exposure.
Measures you can take when a threat is detected
Marking your password in a dark web surveillance scan may be worrisome, but don't panic - it doesn't necessarily mean someone has hacked into your account. It means that your password - or a password related to your account - has been exposed in a data breach. This does not mean being hacked - but it does mean taking measures to protect oneself.
Step 1: Start with safety devices
Before starting to change passwords or take other measures, make sure to use a secure device for operation. If a computer is infected with malicious software such as keyloggers or information theft programs, even newly created passwords may face risks. 💡
Run reliable antivirus or anti malware scanning programs to check for threats. 💡
When managing sensitive accounts, avoid using public or shared computers.
Step 2: Prioritize the most important accounts
Firstly, it is necessary to protect critical accounts:
✔ Email accounts - these accounts are usually the key to resetting other passwords.
✔ Financial accounts - banks, credit cards, and payment platforms should be updated immediately.
✔ Social media and shopping accounts - prevent unauthorized login and potential fraudulent behavior.
If your password is leaked, please change it as soon as possible and ensure that it is strong and unique - the password manager can generate and store these passwords for you.
Step 3: Enable Two Factor Authentication (2FA)
For accounts that support two factor authentication (2FA), please enable this feature. This will add an extra layer of security to ensure that even if your password is leaked, hackers will still not be able to access your account without a second round of verification.
Step 4: Continue using dark web monitoring - this is an ongoing process
Cybercriminals constantly collect and sell stolen credentials - therefore, dark web monitoring is not a one-time scan, but a continuous tool that helps you stay ahead of threats.
Please keep updating your old password, starting with the most important account.
Monitor new alerts and take necessary measures to protect the security of your account.
Step 5: Stay proactive and develop good safety habits
The ultimate goal of dark web monitoring is to ensure the security of accounts, but due to hackers constantly attacking online accounts, security protection is an ongoing process. 💡
Set strong and unique passwords for each account - a password manager can help you. 💡
Be wary of phishing scams and emails claiming account risks. 💡
Regularly check dark web monitoring alerts and take action when necessary. 🔒
Dark web monitoring provides you with professional tools to protect yourself - just like hackers trying to invade using professional tools. The difference is that now you have the upper hand.